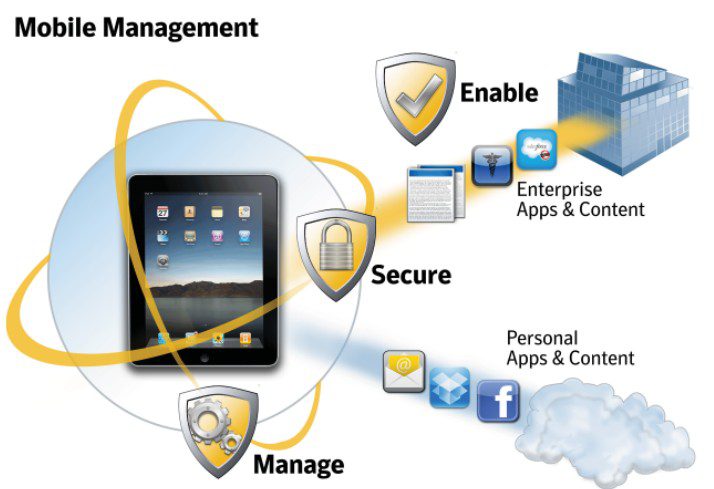
Endpoint Security Management: Securing Today’s Perimeterless Networks
Nathan Colyer-Long2019-08-05T13:22:38+08:00Growing mobile device usage requires comprehensive endpoint device security management.
As the variety of ways workers connect together and to the internet to work expands, so do the steps needed to be taken to ensure those connections are secure and not a risk to your business.
Employees are increasingly using mobile