
Unlock the full potential of your
business with the right IT strategy
Empower your journey towards efficiency and security with Future Logic as your guide.
Together, we'll turn I.T. challenges into your competitive edge.
What Success Looks Like:
In the fast-paced digital world, your business deserves to thrive, not just survive. You’ve faced the complexities of I.T. head on, striving to protect and grow your enterprise. Now, imagine a future where those challenges morph into opportunities. Future Logic stands beside you, not just as a service provider, but as your guiding light towards that future. We understand your aspirations and offer bespoke I.T. solutions designed for success.
Confidence in Every Decision: Knowledge that your I.T. infrastructure supports your business goals, undeterred by the pace of technological change.
Freedom to Focus: Redirecting your attention to where it's most needed, nurturing growth and innovation within your organization.
A Trusted Partnership: Leaning on a reliable partner who anticipates and mitigates risks before they become issues.
Specific strategies tailored to unique challenges, leading to detailed service descriptions.
As your Strategic Managed Service
Provider you can expect:
Strategic Empowerment: Tailored I.T. strategies that align with your business’s core objectives.
Operational Excellence: Streamlined processes and systems for maximum efficiency.
Innovative Edge: Leveraging the latest in I.T. solutions to keep you ahead of the curve.
Problems We Solve
In a world driven by technology, businesses face a myriad of challenges. The landscape is ever-shifting, demands are constantly rising and the stakes have never been higher. At Future Logic, we know these problems because we live in the solutions. You're not alone in this digital maze, and here's how we navigate the common hurdles you're facing.
Overwhelmed by Complexity
Feeling lost in the complexity of I.T. infrastructure management?
Overwhelmed by Complexity:
"We get it. The sheer volume of options and the rapid pace of technological evolution can be daunting. It's easy to feel like you're in over your head."
"Future Logic steps in as your guide, simplifying the complexities. Let's streamline your I.T. together, making technology work for you, not against you."


Cybersecurity Concerns
Worried about the ever-present threat of cyber-attacks?
Cybersecurity Concerns:
"In an age where data breaches are just around the corner, your anxiety is justified. The safety of your digital assets is paramount."
"With Future Logic, fortify your defences. We’re your vigilant protectors in the digital realm, always a step ahead of potential threats."
Inefficient Systems Slowing You Down
Frustrated by inefficiencies that hinder your team's productivity?
Inefficient Systems Slowing You Down:
"Nothing stifles growth like outdated or mismatched systems. The frustration of lost time and resources is all too familiar."
"Embrace efficiency with Future Logic. We refine your I.T. environment for peak performance, ensuring your team can focus on what they do best."


Costly I.T. Investment with Low Return
Investing in I.T. without seeing the growth you expected?
Costly IT Investment with Low Return:
"Technology should be your most powerful investment, not a financial sinkhole. It's crucial that every dollar spent moves you forward."
Maximize your ROI with strategic I.T. planning from Future Logic. Together, we'll ensure your technology investments are wise, targeted and fruitful."
Lack of Strategic I.T. Vision
Struggling to align your I.T. strategy with your business goals?
Lack of Strategic IT Vision:
"An I.T. roadmap disconnected from your business vision can feel like sailing without a compass."
"Future Logic aligns your I.T. trajectory with your business objectives. Let's chart a strategic course to your success, ensuring we're not just solving I.T. problems but paving the way for your future."


Communication Gaps and Absentee Support
Frustrated with I.T. support that's always distant or hard to reach?
Communication Gaps and Absentee Support:
"Effective communication is the cornerstone of any partnership, especially when it comes to managing something as crucial as your I.T. Infrastructure. Dealing with providers who are unavailable or fail to communicate clearly can leave you feeling isolated and unsupported."
"Future Logic champions open, transparent communication and the value of face-to-face interactions. We believe in being more than just a voice on the phone; we're your I.T. partner, ready to meet, discuss and strategise in person. With us, you're always in the loop, ensuring your I.T. solutions truly align with your business needs."
"At Future Logic, we've seen these challenges time and again and guided countless businesses to the other side.
Your journey towards overcoming these obstacles begins with understanding that the right guide can turn these hurdles into stepping stones for growth. Let’s embark on this journey together, transforming challenges into victories."
How We Help
In your journey to conquer the digital landscape, you're the hero at the forefront. Future Logic plays the trusted guide, illuminating the path ahead with bespoke I.T. solutions designed to elevate your business to the next level. Here’s how we turn your I.T. trials into triumphs.
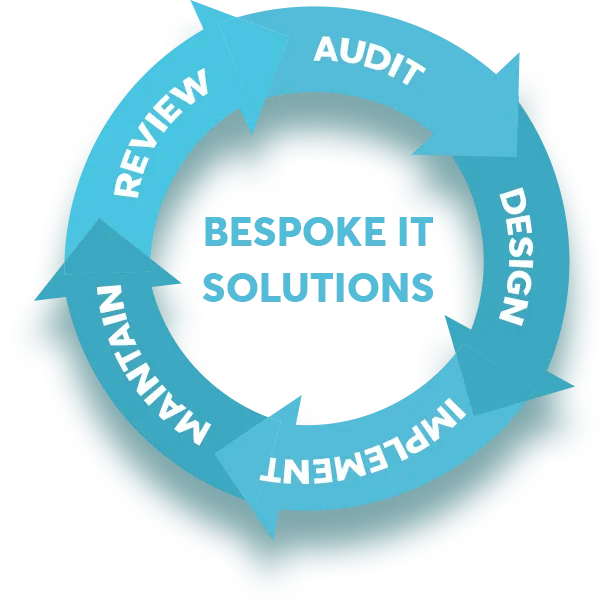
Audit
We begin with an in-depth understanding of your unique business needs, goals and the current I.T. setup.
Design
We develop a strategic I.T. roadmap tailored for your business outlining the current situation, our proposed solutions and a timeline for implementation.
Implement
We develop a strategic I.T. roadmap tailored for your business outlining the current situation, our proposed solutions and a timeline for implementation.
Maintain
We don't just set up and leave – we provide ongoing monitoring and maintenance to ensure your IT systems run smoothly.
Review
We believe in open communication. We provide regular reports on your I.T. system performance and conduct reviews to ensure alignment with your business goals.
With Future Logic's Managed I.T. Services, transform your I.T. struggle into a strategic advantage.
Let us navigate the technological landscape, guiding you towards growth and success.
Empowering Your Journey
With Future Logic as your guide, the path through digital challenges becomes clear and
actionable. Our expertise is your resource, our insights your advantage, and our partner-
ship your pathway to success.
Tailored I.T.
Strategy Design
Tailored IT Strategy Design
Our Role: Imagine us as your strategic counsel, meticulously crafting an I.T. roadmap that aligns seamlessly with your epic quest for growth and efficiency.
Your Journey: You're equipped to navigate the digital domain with confidence, backed by a strategy that leverages technology as a catalyst for your business’s success.
Proactive Monitoring and Maintenance
Proactive Monitoring and Maintenance
Our Role: Consider us your vigilant guardians, proactively overseeing the health of your IT infrastructure to pre-empt threats and prevent downtimes.
Your Journey: Rest assured knowing that your IT environment is under constant watch, allowing you to focus on leading your business to new heights without interruption.
Robust Cybersecurity
Measures
Robust Cybersecurity Measures
Our Role: We stand as your fortress, erecting barriers and implementing cutting-edge security measures to protect your kingdom from digital adversaries.
Your Journey: Navigate the digital world with peace of mind, fortified by the knowledge that your assets are shielded from threats, enabling safe and secure growth.
Efficient
Cloud Solutions
Efficient Cloud Solutions
Our Role: Envision us as your innovators, leveraging the cloud to provide scalable, flexible solutions that promote collaboration and agility.
Your Journey: Embrace the freedom to expand and innovate, unshackled by physical constraints, with cloud solutions that adapt to your evolving quest.
Strategic
I.T. Consulting
Strategic I.T. Consulting
Our Role: We are your sage advisors, offering the wisdom gained from years of experience to guide your decision-making and strategic planning.
Your Journey: Armed with insights and advice, you’re ready to make informed decisions that propel your business forward, turning challenges into opportunities for growth.
Personalised Support
and Communication
Personalised Support and Communication
Our Role: Consider us your reliable companions, always on hand for face-to-face discussions, support, and transparent communication, ensuring you’re never left in the dark.
Your Journey: Feel supported at every turn, with a dedicated team that understands your business and communicates effectively, making complex I.T. issues simple.

About Us
We are your trusted IT advisors and support partners. Our job is to minimise disruption to your business and optimise your productivity- because we all know even a small disruption to a company’s IT system results in a massive flow-on effect to other dependant staff and processes.
Our aim is to make your IT as hassle-free as possible, by reducing disruptions to your productivity.
Conclusion
"At Future Logic, your mission becomes ours. As your guide, we’re committed to empowering you with the tools, strategies and support you need to conquer the I.T. world. Together, we'll transform the landscape of challenges into a realm of opportunities, crafting a story of success where you emerge victorious.
Let’s embark on this journey together, with you as the hero of your story and Future Logic as your guiding light."
Latest News
Latest Blog Posts
Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim
ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.




